“I’ve just notarize an app with Xcode organizer UI. As a next step I want to do it in [a] CI process. How to do it?”
“Is there instruction on how to best integrate [notarization] into a CI build process?”
“How can I get this [notarization tool output] from the command line so the build script can deal with the result?”
Are those questions sound familiar to you? If yes, you’ve come to the right place.
For those who are not in-the-know, notarization in this article is about registering macOS applications—or other executables such as loadable bundles and kernel extensions—to Apple. In turn, Apple would scan those binaries for known malware and then provide a cryptographic stamp of approval. Another key point is that notarization has been mandatory for applications built after 1 June 2019 that are distributed outside the Mac App Store.
What are the benefits of notarization? Why would Apple places this roadblock and create work for developers?
From the users’ perspective, notarization increases the security of their systems. Basically, users would not need to run anti-virus software any longer. Given that all of the user’s installed software is either notarized or comes from the Mac App Store implies that all applications are already scanned for known malware. In essence, users would not need to scan those binaries again. Furthermore, an application’s code signature ensures that it is traceable to either an organization or the individual who produced it. Undeniably this reduces the incentive to deliberately distribute malware. Not to mention that Apple can revoke a signing certificate should the developer has been proven malicious. At any rate, Apple has blocked specific versions of applications before because they were known to contain malware.
From the developers’ perspective, notarization and code signing ensures the integrity of the application. For that reason developers, can trust many more 3rd party distribution channels to transmit their applications without fear of tampering. A few examples include providing copies to users in low-bandwidth areas, distribution to users surrounded by a great firewall, or even distribution through physical media. Furthermore the hardened runtime requirement of notarization improves the application’s run-time security. In particular making it less exploitable by malicious parties—which is important for applications needing to process data from potentially untrusted sources. Finally, notarization is the only viable way to distribute native macOS applications outside the Mac App Store. Thereupon negating the need for sandboxing which may not be appropriate for some application’s design. To emphasize, avoiding the App Store also means avoiding the need (and trouble) to go through App Review.
On the other hand, if you skip the App Store and do not notarize your app, then macOS would refuse to launch your application. In particular, when users double-click on the app bundle, macOS would respond by showing the “YourApp.app cannot be opened because the developer cannot be verified. macOS cannot verify that the app is free from malware.” dialog instead of opening your app.
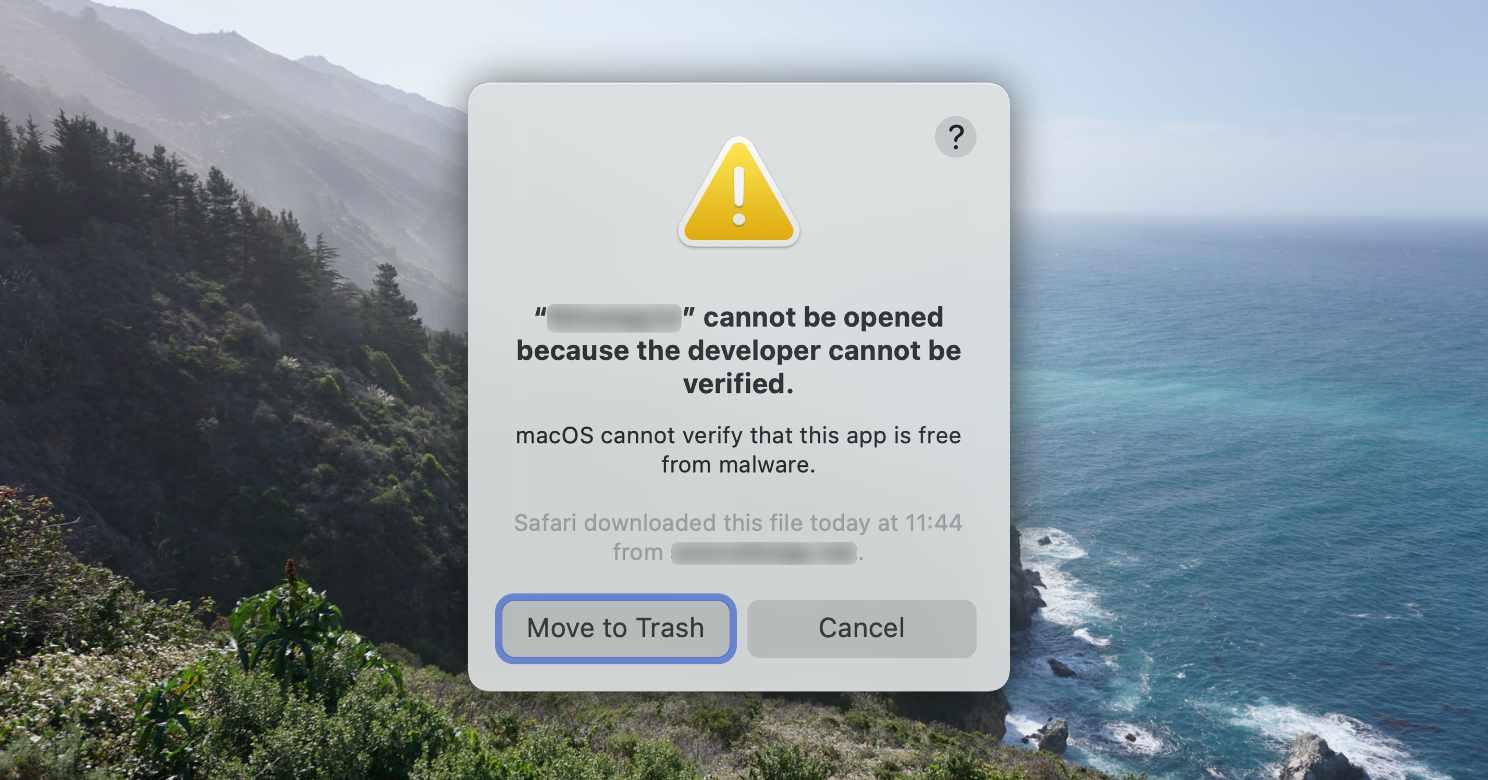
In reality, power users has a way to override the above blocker. Although a few software developer I know wasn’t able to get through this dialog without my help (read: workaround). Then again, they were not macOS developers per se—they just happen to use macs to develop server software.
First thing to remember, signing an application is a prerequisite to notarizing it. Evidently the signed binary carries your organization’s reputation with it. For that reason you would need to secure the code signing certificate—and not to e-mail it nonchalantly to an intern so that s/he can sign and notarize applications for you. To point out, a disgruntled employee may deliberately distribute bad software under your company’s good name—when given access to the company’s code signing certificate and/or notarization credentials. You would’t want that to happen, would you?
To this end, having a secure build machine for Developer ID signing and notarization serves to safeguard the signing certificate as well as notarization creentials. Therefore you can entrust these critical credentials to a few trusted administrators without filling up their time to actually sign and notarize applications on a daily basis.
Wouldn’t it be great if you can automate the notarization process? Together with creating a CI/CD workflow which builds macOS apps, sign, and notarize them without wasting a developer’s brain bandwidth?
What if you already have a CI/CD process? Notably a complex one that produces the same app in multiple variations? Wouldn’t you want to integrate notarization into this pre-existing workflow?
Introducing my latest book: How to Automate macOS Application Notarization (ISBN 978-981-18-2531-6) where you can find:
- An overiew of the notarization workflow, the command line tools involved, and how to control those tools from scripts.
- A step-by-step guide on how to create a CI/CD pipeline for notarization, using Xcode Server as an example.
- A sample shell script for notarization contained in a sample project to test your CI/CD pipeline with.
- A cheat sheet that you can paste on your wall as you integrate notarization into your own environment.
To emphasize, you can save 40–60 hours of trial and errors in writing scripts to automate notarization and integrate it into a CI/CD system.
The book is written with the Dev-Ops person in mind. Then again you could also benefit from the book if you are a software architect, team lead, or development manager who delivers macOS applications—or looking to deliver one. Having prior experience with Xcode would be useful. Although no macOS sofware development experience is required, since all programming in the book are done with Unix shell scripts.
This edition is written with maOS Monterey and Xcode 13 in mind. In particular, it is a PDF e-book that is about 79 pages long and formatted as an A5 paper (about the size of an iPad mini). Correspondingly there is an ePub version available for reading in Apple Books. What’s more there is an accompanying Xcode project containing sample notarization scripts and a cheat sheet that you can paste on your wall.
Still not convinced? You can find the table of content for the book as follows
- Introduction
- About the Book
- Is this for You?
- The Notarization Workflow
- Workflow Elements
- Authorization & Authentication
- Parsing Output
- Command Reference
- Submit
- Get Notarization Log
- Staple Notarization Results
- Product Validation
- Xcode Bot Integration
- Pre-Requisites
- Project Setup
- Server Setup
- Xcode Server Configuration
- Xcode Bot Setup
- Troubleshooting
- Next Steps
- Securing Credentials
- Hardened Runtime
- Non-App Bundles
- Other CI/CD Systems
- About the Author
Satisfaction guaranteed, otherwise I’ll refund your money. Keep in mind that that the book can save you about $2500 worth of effort, based on the median rates of macOS developers listed on Upwork.

0 thoughts on “Introducing macOS Notarization Automation Book”